3 tools for managing third party information security risks in a SaaS company
August 5, 2019
2 min read
1Most of our information security clients provide Software-as-a-Service (Saas) to their customers in verticals such as sales enablement, onboarding, investigation case management and stakeholder management. Across all of these organisations the common risk that is difficult to manage is that which is introduced by third parties whether they are suppliers, contractors or providers of open source software.
It is difficult to manage third parties from an information security perspective but thankfully there are now a number of products available to make this easier. We've cultivated a list of these products as a point of reference for other organisations looking for solutions to the same risks:
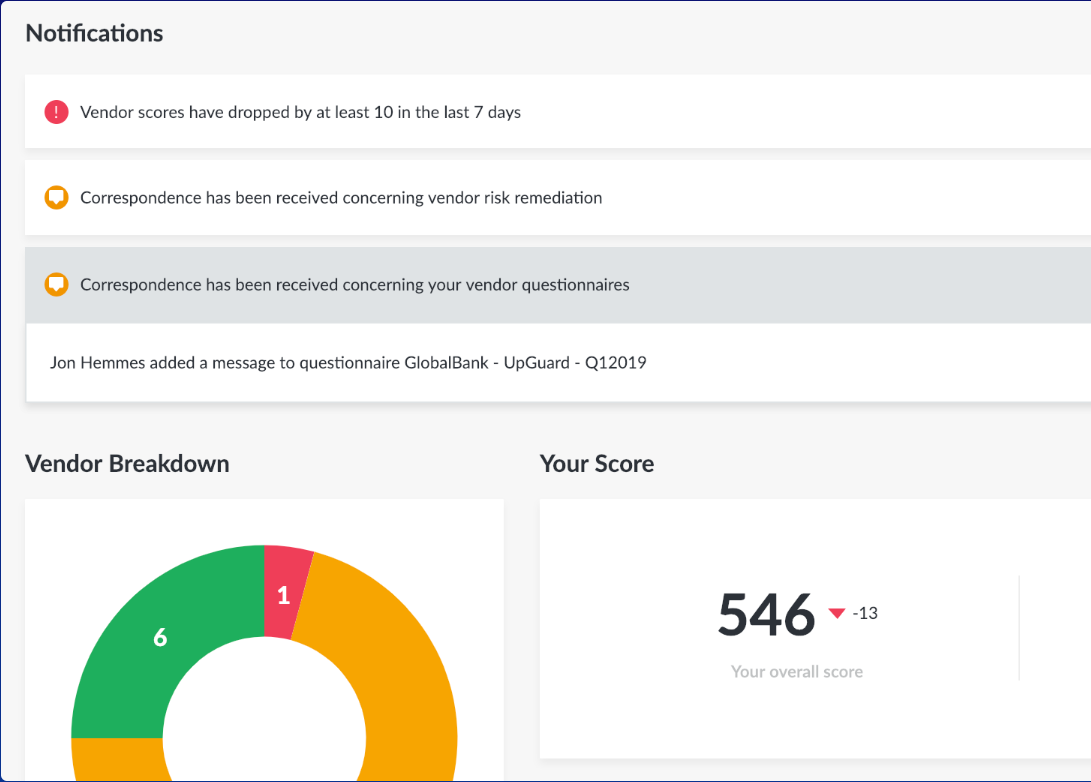
Upguard VendorRisk
Upguard VendorRisk is a product that allows organisations to move away from the manual process of sending out word document or excel based security questionnaires with hundreds of questions to their suppliers and then having to invest a significant amount of time in reviewing the responses and supporting evidence to determine if the supplier meets the organisation's security requirements.
With the use of Upguard VendorRisk an organisation can move to the model of automating security questionnaires and the scoring of suppliers to give you a holistic view of your supplier risk profile. In addition to questionnaires there is the additional function of monitoring the suppliers public facing applications and websites to identify vulnerabilities.
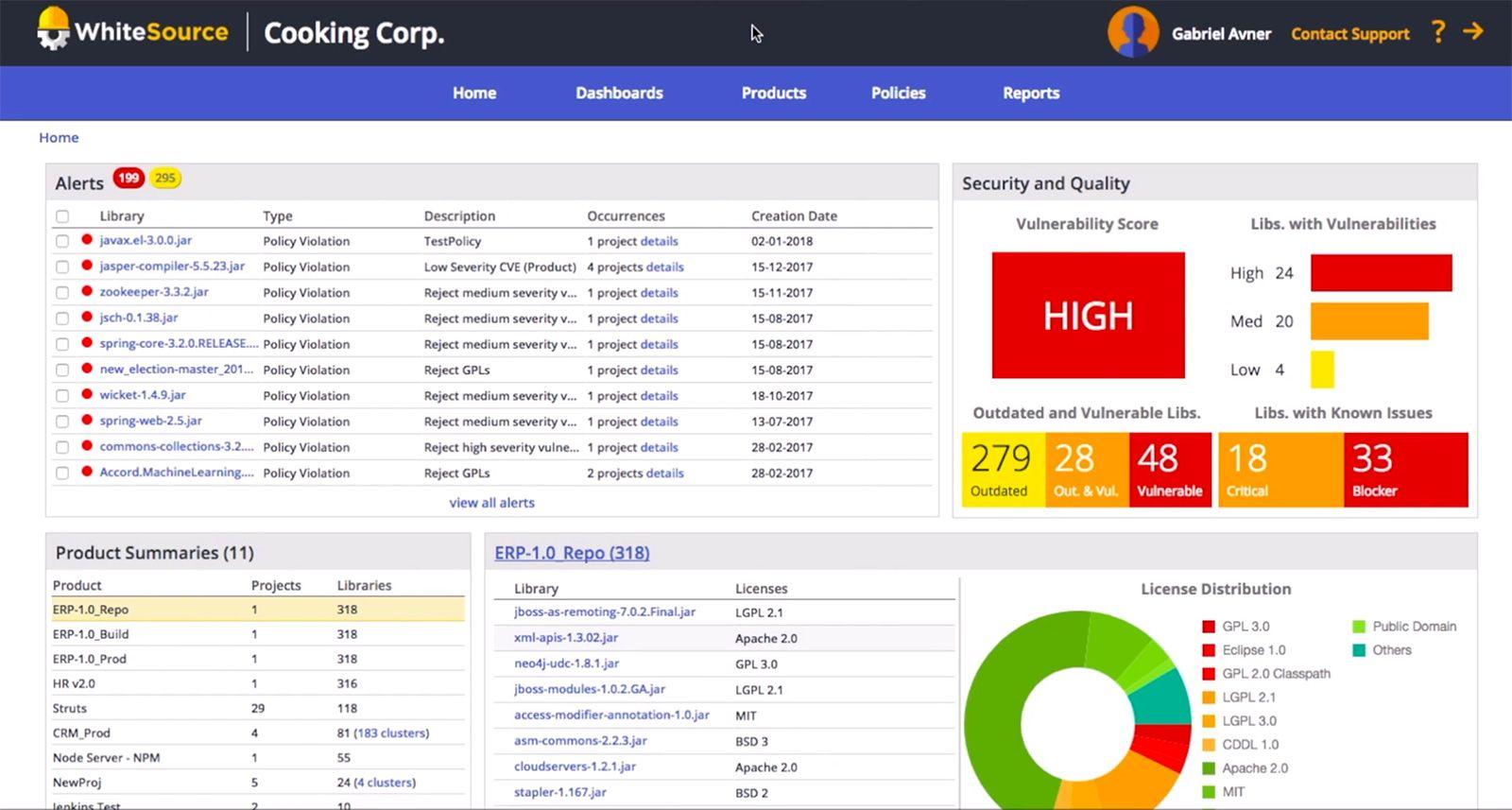
Whitesource
Whitesource is a tool that should be integrated into the software development lifecycle of any SaaS provider given that it addresses the risks of using third party libraries and open source software. Whitesource assists with:
- Vulnerability detection - identify vulnerable open source components across 200 programming languages
- Vulnerability remediation - providing suggestions as to how to remediate the vulnerabilities
- Continuous monitoring - alerting you if a vulnerability is identified in a historic version, detecting vulnerable components using a web browser extension before you download them and enforcing
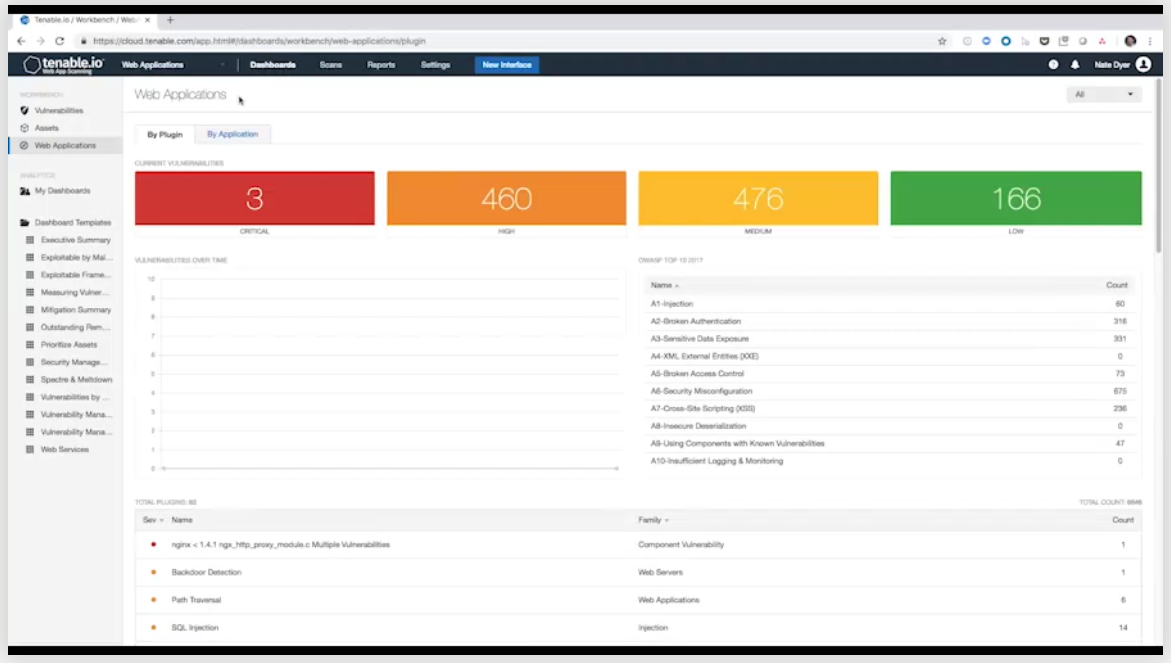
Tenable
Tenable has a number of products depending on your infrastructure and the types of scanning. Automated web application scanning on any frequency that the organisation determines as suitable with grading of findings based on severity and potential impact to the organisation.
The above-mentioned tools have been implemented across multiple clients and as we come across more that are suitable, we will update this article with their details. If you have any suggestions for other tools to review, please reach out to us through the contact us page.
Sign up for our newsletter
Stay Ahead: Subscribe for the Latest Compliance Insights and Updates.
We care about the protection of your data. Read ourPrivacy Policy.


