ISO 27001 Information Security Management System
August 21, 2024
15 min read
55What is an Information Security Management System?
Data and information are valuable assets in every organisation and deserve to be protected from potential risks or threats. To secure your intellectual property, financial data and third party or employee information, you have to implement an Information Security Management System (ISMS).
An ISMS is a combination of processes and policies that help you identify, manage, and protect vulnerable corporate data and information against various risks. Specifically, the ISMS’s key objective is to ensure the confidentiality, integrity and availability of data and information in maintained.
ISO 27001
ISO 27001 is an internationally recognised standard that sets the requirements for an ISMS. These requirements provide you with instructions on how to build, manage, and improve your ISMS. The standard, which was updated in 2022 and is currently referred to as ISO/IEC 27001:2022, is considered the benchmark to maintaining customer and stakeholder confidentiality. According to the results of the ISO Survey of Certifications, in 2022 there were over 70,000 organisations worldwide who had achieved ISO 27001 certification.
Benefits of ISO 27001 certification
If you are a business owner who is thinking about implementing an ISMS in their organisation or a manager in a company who wants to get Senior Management on board with an ISMS, you need to know more about what value ISO 27001 can add to your business. Here we explain some of the major benefits that your organisation can expect to achieve:
Protection from security threats
The most obvious reason to implement ISO 27001:2022 is that it will help your organisation to avoid security threats. This includes both cyber criminals targeting your data and data breaches caused by employees/ contractors either accidentally or intentionally.
A proactive approach to risk management
ISO 27001:2022 helps your organisation to identify the threats toward your information security and create plans to address them. Each risk will have a risk owner assigned, who is responsible for managing the security threat. The risk owner should be someone for whom the risk is relevant to their role and who has the authority to make decisions and take actions regarding the risk. This approach allows your organisation to have visibility over the risks that are relevant to them and proactively implement controls and ownership.
Information security is everybody’s responsibility
Your employees are your first line of defence, however unfortunately the vast majority of security violations and breaches start with users. When becoming ISO 27001 certified, you will increase your employee’s security awareness through training to ensure that they understand the necessary information security policies and procedures. This helps employees to understand how their actions contribute to the overall success of your organisation’s information security management.
ISO 27001 promotes continuous learning and improvement- so as the threats evolve, so do your employees.
A competitive advantage and strengthened reputation
Achieving ISO 27001:2022 certification demonstrates your organisations commitment to maintaining robust information security processes and keeping your clients information safe. This positions your organisation as a trusted partner and distinguishes you from your competitors who are not certified to ISO 27001:2022.
Moreover, ISO 27001 certification is more commonly becoming a requirement for suppliers/ vendors across the private and public sector.
Meets legal or third-party compliance obligations
You may be required by a client, third-party or by law to demonstrate your organisations information security management compliance. By achieving ISO 27001:2022 certification, your organisation holds an internationally recognised best practice framework for the management of information security.
Four facts about ISO 27001:2022 that you need to know
Below are four key facts about ISO 27001:2022 to help you prepare for your ISO 27001:2022 journey.
ISO 27001:2022 is not about documentation
ISO 27001:2022, like other recently updated standards, uses the term documented information, which means an organisation can retain the necessary information in the way that best suits it and to the extent that is needed.
ISO 27001:2022 is uncomplicated
ISO 27001:2022 aims to make the process of implementing an ISMS simple enough that everyone can be a part of it. The framework helps you to identity:
- The policies and procedures that the organisation needs to document.
- The technical controls and technologies required to protect your assets.
- The staff training required to increase awareness and prevent mistakes.
Information Security is not the IT Department's responsibility
Information security is everybody’s responsibility. All employees, regardless of their role must be provided with the necessary information security training so that they aware of how the day to day activities within their role impact information security management.
It is not prescriptive
The framework of ISO 27001:2022 sets the outcomes that are expected to be achieved but how these are achieved is up to the organisation. During an audit you must be able to demonstrate that you have achieved the outcome in a way that aligns with the context of your organisation. Context can include applicable legislation, contractual requirements, expectations from the Board, information security risks or any other item that is specific to your organisation.
ISMS Requirements
Organisations of all sizes and types collect, process, and communicate information in various ways and as such, can benefit from the implementation of an ISMS that aligns with ISO 27001:2022. ISO 27001:2022 includes 93 security controls which are divided into four categories; organisational, people, physical and technological. These are found in Annex A of the Standard.
ISO 27001:2022 also provides organisations with 10 clauses that serve as information security management system requirements. Clause 1 to 3 provide introductory information about terms, definitions and normative references of ISO 27001:2022. The auditable content starts from Clause 4, which we have outlined below:
4- Context of the Organisation
Your organisation’s ISMS will be built around the context of your organisation. Context of the Organisation involves identifying and analysing your business and your environment. To do so, you have to determine all the factors that can affect the success of your ISMS and achieving its goals, including:
- All of the internal and external issues related to the ISMS.
- All of the internal and eternal interested parties and their expectations.
- The scope of the ISMS.
It is very important to define the context of your organisation as this will later inform other important ISO 27001:2022 processes such as risk management and continual improvement. When defining the context of your organisation, the most important thing to achieve is identifying what assets need to be protected within your ISMS and why.
5- Leadership
Involvement and commitment from Top Management plays a key role in the success of an ISMS.
Top Management can do the following to demonstrate their support and engagement:
- Establish the ISMS policy and objectives or an objective framework.
- Align the ISMS policy and objectives with the overall business strategy.
- Integrate the ISMS requirements and controls into other organisation processes.
- Allocate the required resources to the development and implementation of the ISMS.
- Communicating with and supporting people who have a role to play in the implementation of the ISMS.
6- Planning
When planning an ISMS, an organisation should consider any issues that were raised within Clause 4- Context of the Organisation and determine risks and opportunities that need to be addressed. Clause 6 requires organisations to have a risk assessment process in place that defines, determines and addresses the risks, as well as a risk treatment process which identifies appropriate risk treatment options and determines all controls necessary implement the treatment.
As a part of the planning process, it is a requirement for the organisation to produce a Statement of Applicability (SoA). The SoA contains a summary of the 93 security controls, a justification for their inclusion (or exclusion) in the ISMS and whether or not the controls have been implemented.
Additionally, the clause requires the organisation to establish their information security objectives and plans to achieve them, as well as ensuring that all changes to the ISMS are carried out in a planned manner.
7- Support
An adequate level of support is necessary to successfully implement and maintain an ISMS. Support can be provided where there are enough resources, competencies, communications and documented information available.
Resources include people, time, budget, information and infrastructure that might be required in the process of complying to ISO 27001.
Competencies relate to the people involved in the ISMS and their capabilities to perform their roles and responsibilities.
A communication process should be established to ensure that all internal, external and interested parties receive information relating to the ISMS to the extent required. Clear and effective communication is important to ensuring the success of the ISMS.
8- Operation
Once the context of the organisation, risks and opportunities have been defined the next step is to ensure that there are processes in place to meet the requirements.
It is important to ensure that all processes are documented and available to demonstrate that operational processes are carried out as planned.
9- Performance Evaluation
When the required processes are implemented, they must be evaluated to see if the organisation has reached their predefined outcomes. It is important to consider the methods for evaluation, who will evaluate and how the results of the evaluation should be analysed. As a part of the evaluation phase, important questions to ask include:
- How is the information security performance?
- How effective is the ISMS?
10- Improvement
The organisation must continually improve the suitability and effectiveness of the ISMS to align to its context. As the context of the organisation is subject to constant changes, improving the ISMS should be an ongoing process and a critical component of an effective ISMS.
Annex A
Annex A outlines the 93 security controls that an organisation should consider as a part of their SoA. Please find an outline of the controls below:
| Control Group | Controls |
|---|---|
Governance |
|
Asset Management |
|
Incident Management |
|
Supplier Relationships Security |
|
Identity and Access Management |
|
System and Network Security |
|
Legal and Compliance |
|
Information Security Assurance |
|
Threat and Vulnerability Management |
|
Information Protection |
|
Application Security |
|
Secure Configuration |
|
Physical Security |
|
Continuity |
|
Human Resource Security |
|
Risk Management and Security Controls
ISO 27001:2022 considers information security risk management to be the foundation of an ISMS and requires organisations to have a process for risk identification and risk treatment. Through this process, businesses can fully leverage the benefits of an ISMS.
In simple terms, risks can be thought of as anything that could go wrong within the scope of your ISMS e.g. a data breach, damaged server, service outage or hacked bank account. Implementing a risk management process can be achieved by following the below steps:
Step 1- Development of a Risk Register and Risk Identification
Develop a risk register, including an agreed methodology for identifying and assessing risks. Identify all of the risks within the scope of your ISMS that could compromise the confidentiality, integrity and availability of information.
Step 2- Risk Owner Identification
Determine who is responsible for each risk. The risk owner should be someone for whom the risk is relevant to their role and who has the authority to make decisions regarding the risk.
Step 3- Risk Prioritisation
Determine the consequences and likelihood of all risks. This will enable you to prioritise the risks based on the possibility of their occurrence and the severity of the results.
Step 4- Controls and Statement of Applicability (SoA)
Associate each risk with one or more appropriate controls from ISO/IEC 27001:2022, Annex A. There are 93 controls in Annex A which include policies, processes, procedures, organisational structures, hardware and software functions that you can implement to address risks to your ISMS.
Once completed, create your SoA, which contains the applicable security controls along with justifications as to why the controls have or have not been included in the SoA and a status that indicates whether or not the control has been implemented.
Step 5- Risk Treatment Plan
Create the risk treatment plan. While ISO 27001:2022 does not have a prescriptive framework for this, the risk treatment plan should include:
- The controls that need to be implemented.
- The control status.
- The risk owners who are responsible for implementing the controls and ongoing monitoring of their performance.
The risk treatment plan should be documented in and stored within the risk register.
Certification to ISO 27001
What does an ISO certification body do: Stage 1 and Stage 2 audit with a certification body
Third Party Certification is the process of having your Information Security Management System audited by an independent third party. This type of auditing is typically used by Conformity Assessment Bodies (CABs) who are regulated by a government organisation known as JAS-ANZ. These CABs can issue registered certificates of compliance to various standards such as ISO 9001, ISO 45001, and ISO 14001.
Stage 1 and Stage 2
The formal assessment process includes two stages. In Stage 1, the auditing body will confirm whether you have met the requirements of your proposed scope and the objectives that your organisation has set. If the auditing body finds any areas of concern, you will have time to address these before the beginning of the Stage 2 audit.
During the Stage 2 audit, your system will be assessed again to identify any nonconformities (which indicate a lapse in the implementation of your ISMS processes) and make sure that all areas of concern have been rectified. At this point, if there are no major nonconformances your certification can be issued. Otherwise, you will be given time to correct existing nonconformities before the next visit of the Auditor and only after removing all major nonconformities will your organisation be eligible for ISO 27001 certification.
Surveillance audit
Typically, the certification body will conduct an annual surveillance audit of your management system for the first three years after your certification is issued. This ensures your ISMS continues to meet the requirements of ISO 27001:2022 after the initial certification has been achieved.
Transition from ISO 27001:2013 to ISO 27001:2022
If your organisation is already certified to ISO 27001:2013, you will need to transition to ISO 27001:2022 by October 2025.
Contact us to find out more about the key changes that have been made and to find out about how Compliance Council can assist your organisation with the transition.
What’s Next?
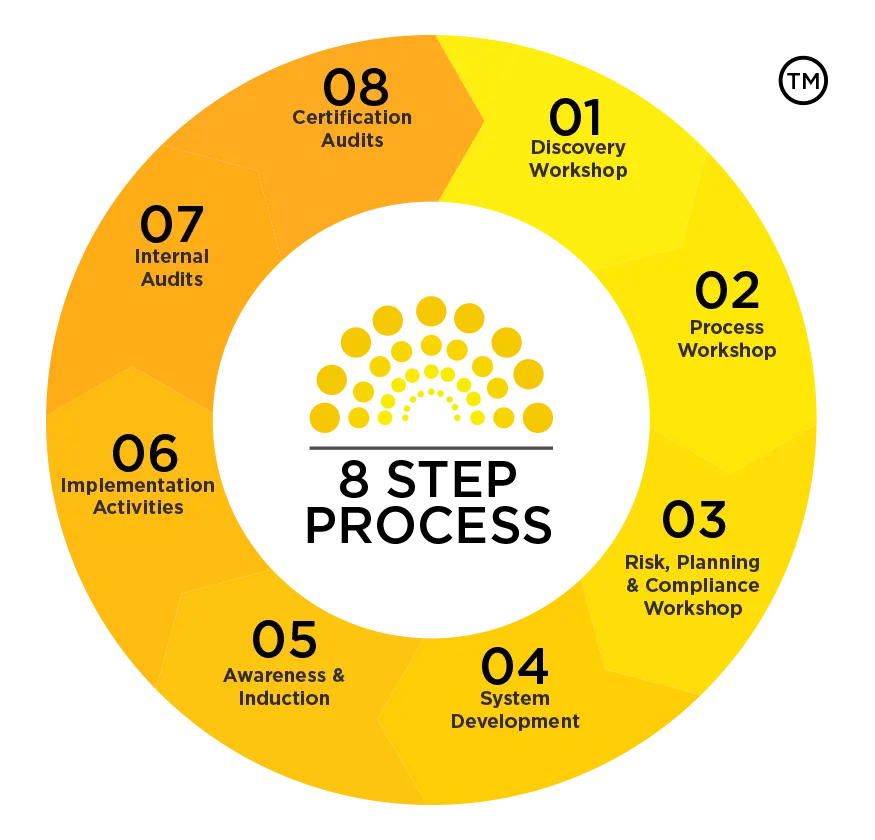
Compliance Council can help your organisation simplify the process of achieving ISO 27001:2022 certification. We have developed an 8 Step Process to assist you with developing and implementing a management system that complies with ISO 27001:2022 and have experience with working with organisations of all sizes, across a wide range of industries.
Frequently Asked Questions
As a leading provider of information security consultancy services we have worked with clients across a wide range of industries including construction, education, architecture, engineering, financial services and SaaS providers among many more.
ISO 27001 applies to any type of organisation, regardless of the size (small, medium, large, nature (public or private) or its core business operations.
We have experience with developing and implementing management systems for organisations ranging in size and complexity including SMEs through to ASX listed organisations.
An Information Security Management System (ISMS) alone won’t add any value to your business or your staff. If the ISMS is designed to fit into the existing operations of the business, and with input from the expected staff who will be using the system, then you will start seeing improvement.
You can expect the following improvements from implementing an ISMS:
- Reduced cyber security risks
- Protection of personal records and sensitive business information
- A proactive approach the management of risks
- Increased awareness of information security and information security becoming everybody’s responsibility
- If certified, recognition from your customers for achieving certification and increased confidence from prospective customers
These are some of the benefits of an ISMS although there are many more that an organisation can achieve if it adopts the system into its core operations.
Third Party Certification is the process of having your Management System audited by an independent third party. This type of auditing is typically used by Conformity Assessment Bodies (CABs) who are regulated by a government organisation known as JAS-ANZ. These CABs can issue registered certificates of compliance to various standards such as ISO 27001, ISO 9001, ISO 45001 and ISO 14001.
Unlike many competitors who operate by a time and materials model, we operate by a fixed-fee model. We provide clients with proposals that outline the methodology for the project, the deliverables, and the total cost.
Separately on your end, you'll need to engage the external third-party certification company whose cost will be in addition to our cost. We can definitely put you in touch with certification companies
Yes, the initial consultation meeting with you to gauge what certification would be suitable for the business and also get an understanding of how the business works is free so that we can provide an accurate proposal.
9-12 months (client preparedness plays a major role here).
If there is a tender or client demand for urgency, we and the Certification company can write you a Letter of Commencement, upon request.
Contact us today to discuss how Compliance Council can assist your organisation with complying with ISO 27001.
Contact UsSign up for our newsletter
Stay Ahead: Subscribe for the Latest Compliance Insights and Updates.
We care about the protection of your data. Read ourPrivacy Policy.


